尋夢新聞LINE@每日推播熱門推薦文章,趣聞不漏接❤️
本文來自 雪花新聞,本文標題:WPSeku – WordPress漏洞掃描工具 ,轉載請保留本聲明!
if (window.location.host != ‘www.xuehua.us’){window.location.href=’https://www.xuehua.us/2018/08/02/wpseku-wordpress%e6%bc%8f%e6%b4%9e%e6%89%ab%e6%8f%8f%e5%b7%a5%e5%85%b7′;}
說到wordpress漏洞掃描就不得不提wpscan,他們維護了一個針對wp的漏洞庫,是一個十分強大的掃描器,該工具與其相似,但是又有一個強大的漏洞,就是可以針對本地的wp插件的php代碼靜態掃描
Installation$ git clone https://github.com/m4ll0k/WPSeku.git wpseku$ cd wpseku$ pip3 install -r requirements.txt$ python3 wpseku.py
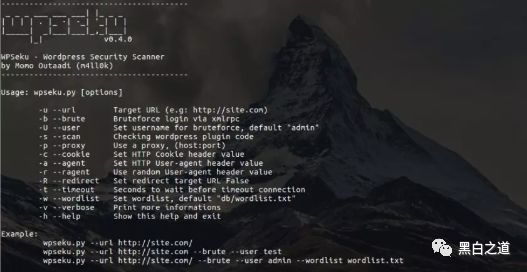
Usage
Generic Scan
python3 wpseku.py –url https://www.xxxxxxx.com –verbose
- Output
—————————————- _ _ _ ___ ___ ___| |_ _ _ | | | | . |_ -| -_| ‘_| | ||_____| _|___|___|_,_|___| |_| v0.4.0WPSeku – WordPress Security Scannerby Momo Outaadi (m4ll0k)—————————————-[ + ] Target: https://www.xxxxxxx.com[ + ] Starting: 02:38:51[ + ] Server: Apache[ + ] Uncommon header “X-Pingback” found, with contents: https://www.xxxxxxx.com/xmlrpc.php[ i ] Checking Full Path Disclosure…[ + ] Full Path Disclosure: /home/ehc/public_html/wp-includes/rss-functions.php[ i ] Checking wp-config backup file…[ + ] wp-config.php available at: https://www.xxxxxxx.com/wp-config.php[ i ] Checking common files…[ + ] robots.txt file was found at: https://www.xxxxxxx.com/robots.txt[ + ] xmlrpc.php file was found at: https://www.xxxxxxx.com/xmlrpc.php[ + ] readme.html file was found at: https://www.xxxxxxx.com/readme.html[ i ] Checking directory listing…[ + ] Dir “/wp-admin/css” listing enable at: https://www.xxxxxxx.com/wp-admin/css/[ + ] Dir “/wp-admin/images” listing enable at: https://www.xxxxxxx.com/wp-admin/images/[ + ] Dir “/wp-admin/includes” listing enable at: https://www.xxxxxxx.com/wp-admin/includes/[ + ] Dir “/wp-admin/js” listing enable at: https://www.xxxxxxx.com/wp-admin/js/……
Bruteforce Login
python3 wpseku.py –url https://www.xxxxxxx.com –brute –user test –wordlist wl.txt –verbose
Scan plugin,theme and wordpress code
python3 wpseku.py –scan <dir/file> –verbose
Note: Testing Akismet Directory Plugin https://plugins.svn.wordpress.org/akismet
- Output
—————————————- _ _ _ ___ ___ ___| |_ _ _ | | | | . |_ -| -_| ‘_| | ||_____| _|___|___|_,_|___| |_| v0.4.0WPSeku – WordPress Security Scannerby Momo Outaadi (m4ll0k)—————————————-[ + ] Checking PHP code…[ + ] Scanning directory…[ i ] Scanning trunk/class.akismet.php file———————————————————————————————————-| Line | Possibile Vuln. | String |———————————————————————————————————-| 597 | Cross-Site ing | [b”$_GET[‘action’]”, b”$_GET[‘action’]”] || 601 | Cross-Site ing | [b”$_GET[‘for’]”, b”$_GET[‘for’]”] || 140 | Cross-Site ing | [b”$_POST[‘akismet_comment_nonce’]”, b”$_POST[‘akismet_comment_nonce’]”] || 144 | Cross-Site ing | [b”$_POST[‘_ajax_nonce-replyto-comment’]”] || 586 | Cross-Site ing | [b”$_POST[‘status’]”, b”$_POST[‘status’]”] || 588 | Cross-Site ing | [b”$_POST[‘spam’]”, b”$_POST[‘spam’]”] || 590 | Cross-Site ing | [b”$_POST[‘unspam’]”, b”$_POST[‘unspam’]”] || 592 | Cross-Site ing | [b”$_POST[‘comment_status’]”, b”$_POST[‘comment_status’]”] || 599 | Cross-Site ing | [b”$_POST[‘action’]”, b”$_POST[‘action’]”] || 214 | Cross-Site ing | [b”$_SERVER[‘HTTP_REFERER’]”, b”$_SERVER[‘HTTP_REFERER’]”] || 403 | Cross-Site ing | [b”$_SERVER[‘REQUEST_TIME_FLOAT’]”, b”$_SERVER[‘REQUEST_TIME_FLOAT’]”] || 861 | Cross-Site ing | [b”$_SERVER[‘REMOTE_ADDR’]”, b”$_SERVER[‘REMOTE_ADDR’]”] || 930 | Cross-Site ing | [b”$_SERVER[‘HTTP_USER_AGENT’]”, b”$_SERVER[‘HTTP_USER_AGENT’]”] || 934 | Cross-Site ing | [b”$_SERVER[‘HTTP_REFERER’]”, b”$_SERVER[‘HTTP_REFERER’]”] || 1349 | Cross-Site ing | [b”$_SERVER[‘REMOTE_ADDR’]”] |———————————————————————————————————-[ i ] Scanning trunk/wrapper.php file[ + ] Not found vulnerabilities[ i ] Scanning trunk/akismet.php file———————————————–| Line | Possibile Vuln. | String |———————————————–| 55 | Authorization Hole | [b’is_admin()’] |———————————————–[ i ] Scanning trunk/class.akismet-cli.php file[ + ] Not found vulnerabilities[ i ] Scanning trunk/class.akismet-widget.php file[ + ] Not found vulnerabilities[ i ] Scanning trunk/index.php file[ + ] Not found vulnerabilities[ i ] Scanning trunk/class.akismet-admin.php file——————————————————————————————————————–| Line | Possibile Vuln. | String |——————————————————————————————————————–| 39 | Cross-Site ing | [b”$_GET[‘page’]”, b”$_GET[‘page’]”] || 134 | Cross-Site ing | [b”$_GET[‘akismet_recheck’]”, b”$_GET[‘akismet_recheck’]”] || 152 | Cross-Site ing | [b”$_GET[‘view’]”, b”$_GET[‘view’]”] || 190 | Cross-Site ing | [b”$_GET[‘view’]”, b”$_GET[‘view’]”] || 388 | Cross-Site ing | [b”$_GET[‘recheckqueue’]”] || 841 | Cross-Site ing | [b”$_GET[‘view’]”, b”$_GET[‘view’]”] || 843 | Cross-Site ing | [b”$_GET[‘view’]”, b”$_GET[‘view’]”] || 850 | Cross-Site ing | [b”$_GET[‘action’]”] || 851 | Cross-Site ing | [b”$_GET[‘action’]”] || 852 | Cross-Site ing | [b”$_GET[‘_wpnonce’]”, b”$_GET[‘_wpnonce’]”] || 868 | Cross-Site ing | [b”$_GET[‘token’]”, b”$_GET[‘token’]”] || 869 | Cross-Site ing | [b”$_GET[‘token’]”] || 873 | Cross-Site ing | [b”$_GET[‘action’]”] || 874 | Cross-Site ing | [b”$_GET[‘action’]”] || 1005 | Cross-Site ing | [b”$_GET[‘akismet_recheck_complete’]”] || 1006 | Cross-Site ing | [b”$_GET[‘recheck_count’]”] || 1007 | Cross-Site ing | [b”$_GET[‘spam_count’]”] || 31 | Cross-Site ing | [b”$_POST[‘action’]”, b”$_POST[‘action’]”] || 256 | Cross-Site ing | [b”$_POST[‘_wpnonce’]”] || 260 | Cross-Site ing | [b’$_POST[$option]’, b’$_POST[$option]’] || 267 | Cross-Site ing | [b”$_POST[‘key’]”] || 392 | Cross-Site ing | [b”$_POST[‘offset’]”, b”$_POST[‘offset’]”, b”$_POST[‘limit’]”, b”$_POST[‘limit’]”] || 447 | Cross-Site ing | [b”$_POST[‘id’]”] || 448 | Cross-Site ing | [b”$_POST[‘id’]”] || 460 | Cross-Site ing | [b”$_POST[‘id’]”, b”$_POST[‘url’]”] || 461 | Cross-Site ing | [b”$_POST[‘id’]”] || 464 | Cross-Site ing | [b”$_POST[‘url’]”] || 388 | Cross-Site ing | [b”$_REQUEST[‘action’]”, b”$_REQUEST[‘action’]”] || 400 | Cross-Site ing | [b”$_SERVER[‘HTTP_REFERER’]”, b”$_SERVER[‘HTTP_REFERER’]”] |——————————————————————————————————————–[ i ] Scanning trunk/class.akismet-rest-api.php file[ + ] Not found vulnerabilities
文章出處:黑客工具箱










